#Onpatrol4malware Blog
Industry News, Updates, and Press Releases
InfoSec Articles (09/12/2022 – 09/29/2022)
Over the last two weeks, we saw that while monitoring the Emotet botnet current activity, security researchers found that the Quantum and BlackCat...
InfoSec Articles (08/29/2022 – 09/12/2022)
Over the last two weeks, we saw the new BianLian ransomware gang, used subtle techniques to exploit, enumerate, and move laterally in victim...
Malware Hashes and Hash Functions
An Introduction to Malware Hashes and Hash Functions Malware hashes are found everywhere in our industry. And for a good reason. They...
InfoSec Articles (08/16/2022 – 08/29/2022)
Over the last few weeks the news of hackers build phishing pages using AWS apps. Also find here the threat alert - cloud network bandwidth now...
InfoSec Articles (08/01/2022 – 08/16/2022)
Over the last two weeks, SC Media shared the top three email-based threats, what they have in common and how you can protect your organization....
InfoSec Articles (07/19/2022 – 08/01/2022)
Over the last two weeks, we saw the DUCKTAIL, infostealer Malware that is targeting Facebook Business Accounts. Also, Palo Alto release the new...
InfoSec Articles (07/04/2022 – 07/19/2022)
Over the past two weeks, we saw the news about the infected WordPress site that revealed a malicious C&C script. Also, a new Android malware...
InfoSec Articles (06/20/2022 – 07/04/2022)
Over the last two weeks, we saw that relevant article "Dark Web Price Index 2022" - "As the global health crisis ground on for a second year, many...
MISP Project – A free & robust open source threat intelligence platform
The MISP project is a free open source threat intelligence platform (TIP) that stores, analyzes, and shares information about malware.It...
InfoSec Articles (06/06/2022 – 06/20/2022)
Over the last two weeks, we saw that a few months back, researchers discovered a new, undetected malware that acts in this parasitic nature...
InfoSec Articles (05/23/2022 – 06/06/2022)
Over the last two weeks, we saw the Clipminer malware gang stole $1.7M by hijacking crypto payments. According to researchers from Symantec, a...
InfoSec Articles (05/09/2022 – 05/23/2022)
Over the past two weeks, we saw The CrowdStrike Falcon OverWatch threat hunting team has uncovered a new and highly sophisticated Internet...
InfoSec Articles (04/25/2022 – 05/09/2022)
Over the last two weeks, we saw new LinkedIn scams, where cybercriminals attack when we may be at our most vulnerable - here's what to look out for...
InfoSec Articles (04/11/2022 – 04/25/2022)
Over the past two weeks, we saw that In February 2022, CISA, FBI, the U.S. CCNMF, the United Kingdom’s NCSC-UK, and NSA released a joint statement...
Threat Intelligence Providers vs Threat Intelligence Platforms
In information security, the ability to predict and adapt to the behaviors of criminals can help organizations improve defense strategies against...
FortiSIEM Configuration Guide
Malware Patrol + FortiSIEMMalware Patrol offers (5) Enterprise* feeds formatted for integration into FortiSIEM. This allows users to combine the...
pfSense Configuration guide
pfSense The pfSense project is a free network firewall distribution, based on the FreeBSD operating system with a custom kernel and it also includes...
DNS Sinkholes Detect and Protect
Bots don't sleep, ransomware finds new ways to infiltrate systems and yesterday's defenses may be ineffective tomorrow. Cybersecurity...
Avoiding Black Friday Phishing Scams
Black Friday is coming and threat actors are already surfing this wave of retail insanity. Not surprisingly, phishing remains an...
MISP Configuration Guide
MISP is a threat intelligence platform for gathering, sharing, storing, and correlating indicators of compromise of targeted attacks,...
Fortinet Configuration Guide
FortiGate NGFWs deliver industry-leading enterprise security for any edge at any scale with full visibility and threat protection. Organizations can...
Mikrotik Router Configuration
Malware Patrol provides a Mikrotik-compatible version of our Malicious Domains and the Tor Exit Nodes data feeds. In this Mikrotik...
What is Ransomware?
Malware Patrol's CEO Andre Correa was recently interviewed by Dana Mantilia from Identity Protection Planning. They discussed the basics - and more...
Best Practices to Protect Against Ransomware
Everyone wants to know how to protect against ransomware - 2021 is the year of ransomware! The Colonial Pipeline attack shutdown a major oil...
Malware Patrol Data Offered in ThreatBlockr Marketplace
Updated on 2022.03.22 - Bandura Cyber now is ThreatBlockr.Press Release  St. Petersburg, FL, July 28, 2021 -- Malware Patrol, the...
InfoSec Articles (06/21/21 – 07/05/21)
Malware patrol selected some relevant news over the past 2 weeks. Microsoft has confirmed signing a malicious driver being distributed within gaming...
InfoSec Articles (06/07/21 – 06/21/21)
In the last two weeks of June, we saw the Japanese multinational conglomerate Fujifilm said it has refused to pay a ransom demand to the cyber gang...
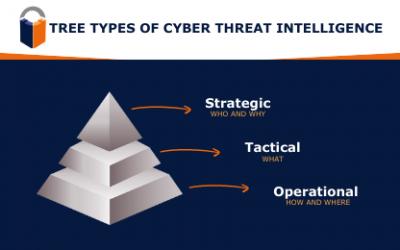
Three Types of Cyber Threat Intelligence
Cyber Threat Intelligence (CTI) is one of the main pillars of cybersecurity. Although it is not the answer to all problems, CTI is one of the most...
DoH! Not so great to the Enterprise
DoH, or DNS over HTTPS (RFC 8484), is a relatively new protocol that provides increased privacy and security. It does this by encrypting DNS queries...
Newly Registered Domains Related to COVID-19
The current outbreak of the COVID-19 created a perfect scenario for all sorts of scammers to monetize through fear, false promises and...
Why Commercial Threat Intelligence Beats OSINT
Picture this: you’re in need of a new suit. You see that your favorite store is giving away designer suits for free and the pictures look...
Threat Intelligence: Essential For Your Cyber Defenses
Cyber risk is growing while confidence in internal defense resilience declining. According to Microsoft’s 2019 Global Cyber Risk Perception...
Palo Alto MineMeld Configuration Guide
Palo Alto MineMeld is an extensible Threat Intelligence processing framework and the multi-tool of threat indicator feeds. MineMeld can...
Postpassword Security with FIDO2
Welcome to the dawn of the post-password world. Multifactor authentication orbits it and two-factor authentication is just a short ride away. A new...
Synergistic Malware Threats
It’s easy to focus on the different kinds of malware threats. Data exfiltration, phishing, ransomware, Trojans, cryptomining and all the other...
Tips for Establishing Your Security Program
(And How the Cyber Insurance Industry May Help You for Free) I won’t keep you waiting. Before you get too excited about that free assist from the...
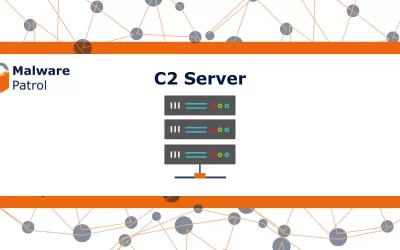
Command and Control Servers: Fundamentals and a Few Details
Few topics in current cybersecurity generate as much press as command and control servers (C2s). They enable the cybercrime that often affects companies and individuals far outside the IT industry.
Whitelisting for Block Lists
Malware Patrol's #1 goal is to protect customers from malware and ransomware infections. These days, this can mean blocking mainstream domains....
Is Online Privacy the Next Phase of Globalization
Google’s first privacy fine post-GDPR sounds substantial. $57 million could certainly buy a first-class infosec infrastructure for a medium-sized...
Phishing’s Next Wave: AI-Enabled Tactics for Attackers and Cybersecurity Pros
Cybercrime steals an estimated $600 billion from the global economy every year. In the next several years we can expect that number to reach well...
Phishing: The Tide Is Still Coming In
In cybersecurity the familiar is dangerous. Because of this, we must qualify what we “already know†and refresh our knowledge. Without this...
Reputation Jacking: Unknown Threats on Well-Known Sites
Threat actors place malicious content on trusted sites to gain access to user’s devices and spread malware. Instead of an outside attack, they wait for the victim to download software from a trusted source or otherwise insinuate themselves into a normal operation.
SpamAssassin Configuration Guide
Malware Patrol provides block lists compatible with SpamAssassin. "Apache SpamAssassin is the #1 Open Source anti-spam platform...
Why choose Malware Patrol over a free DNS protection service?
Customers and prospects have approached us recently with questions similar to this: why should we choose Malware Patrol instead of a free DNS...
Accessing threat data on AWS S3 buckets
Malware Patrol provides some of its threat data feeds via Amazon / AWS S3 buckets. Among the feeds are the "Malware Samples (Binaries)"...
Malware Patrol – Protection Against Crypto Mining Abuse
Cryptocurrency mining as a service is a growing website monetization trend, especially popular on gaming and torrent sites, in which a...
DNS RPZ Firewall Configuration Guide
BIND is the world's most used DNS server and can be configured as a DNS Firewall using RPZ files (DNS RPZ). Response Policy Zone (RPZ)...
Cisco ASA FirePOWER Configuration Guide
“With Cisco ASA with FirePOWER Services, you consolidate multiple security layers in a single platform, eliminating the cost of buying and...
Spoofed DDoS Attacks and BCP 38
The majority of recent DDoS attacks utilize source address spoofing techniques. These spoofed DDos attacks complicate mitigation efforts...
DDoS: What is a Reflection and Amplification Attack?
 Updated on 06/13/2022 DDoS - What is it? A distributed denial-of-service (DDoS) attack is a type of cyber attack in which a malicious...
Popular Domains Hosting Malware
Malware Patrol has maintained a database of malicious URLs and IOCs since 2005. We often receive emails from our users about...
Role of DGAs (Domain Generation Algorithms) in Malware and Ransomware Campaigns
The vast majority of active malware and ransomware families include some sort of communication with command and control systems...
pfBlockerNG Configuration Guide
Malware Patrol provides block lists compatible with pfBlockerNG, a package for pfSense version 2.x that allows the usage of custom block...
Comparing Protection Mechanisms
In a market full of products and services that promise to solve the most varied security threats, it is important to put solutions into perspective, understand what they really deliver and never forget that no single vendor can protect from all threats.
ClamAV Configuration Guide
ClamAV is an open source ant-virus engine for detecting trojans, viruses, malware & other malicious threats. Malware Patrol provides signatures...
Squid3 Web Proxy Configuration Guide
Squid is a proxy for the web that provides extensive access control lists, reduces bandwidth consumption and improves response times by caching and...
BIND9 Configuration Guide
Bind is the world’s most used DNS server. Keep reading to learn how to configure Bind9 to work with Malware Patrol's data. Getting Started Malware...