 Cryptocurrency mining as a service is a growing website monetization trend, especially popular on gaming and torrent sites, in which a JavaScript code utilizes the visitor’s CPU for cryptocurrency mining purposes. While promoted as an alternative to online ads, it is frequently being employed without users’ consent. The most popular service, Coinhive, offers three monetizing methods: 1) a JavaScript executed while the customer browses the site; 2) a “proof of work” (a certain amount of mining) required to bypass a CAPTCHA when submitting a form; 3) or proof of work required on link redirects. The efficacy of these methods is highly dependent on the user’s CPU and the amount of time spent in the website or game. Cryptocurrency mining service providers, including Coinhive and JSE Coin, continue to promote and defend their mining scripts as “an alternative to intrusive ads and dubious marketing tactics”. A screenshot from Coinhive’s website reveals more of their service’s touted benefits:
Cryptocurrency mining as a service is a growing website monetization trend, especially popular on gaming and torrent sites, in which a JavaScript code utilizes the visitor’s CPU for cryptocurrency mining purposes. While promoted as an alternative to online ads, it is frequently being employed without users’ consent. The most popular service, Coinhive, offers three monetizing methods: 1) a JavaScript executed while the customer browses the site; 2) a “proof of work” (a certain amount of mining) required to bypass a CAPTCHA when submitting a form; 3) or proof of work required on link redirects. The efficacy of these methods is highly dependent on the user’s CPU and the amount of time spent in the website or game. Cryptocurrency mining service providers, including Coinhive and JSE Coin, continue to promote and defend their mining scripts as “an alternative to intrusive ads and dubious marketing tactics”. A screenshot from Coinhive’s website reveals more of their service’s touted benefits: 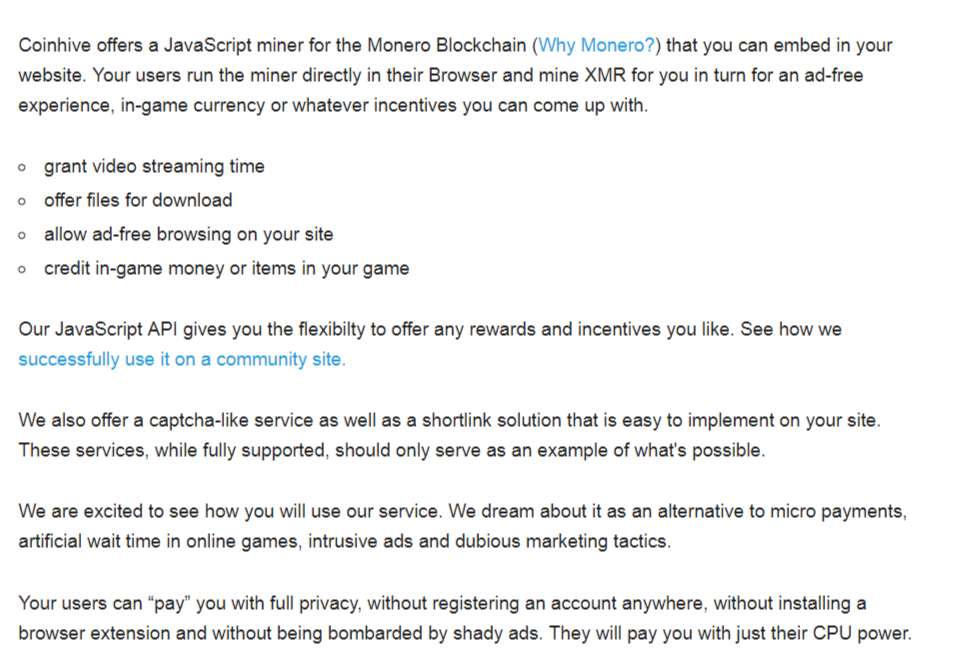 A recent high profile case has brought even more attention to the potential abuses of cryptocurrency mining services. BleepingComputer and Gizmodo, among others, reported on the presence of Coinhive’s Monero Blockchain JavaScript miner on two of Showtime’s websites. The script has since been removed. It is still unconfirmed if this was intentional or the result of a hack. At the time of this article, most sources also stated that Showtime had refused to comment. This undisclosed miner script usage was recently coined as ‘drive-by mining’ by Malware Intelligence Analyst Jérôme Segura in his article on the subject:
A recent high profile case has brought even more attention to the potential abuses of cryptocurrency mining services. BleepingComputer and Gizmodo, among others, reported on the presence of Coinhive’s Monero Blockchain JavaScript miner on two of Showtime’s websites. The script has since been removed. It is still unconfirmed if this was intentional or the result of a hack. At the time of this article, most sources also stated that Showtime had refused to comment. This undisclosed miner script usage was recently coined as ‘drive-by mining’ by Malware Intelligence Analyst Jérôme Segura in his article on the subject:
“Because mining happens in the browser via JavaScript without user interaction, we could compare it to drive-by downloads. As publishers need to retain the visitor’s attention so that the JavaScript code runs uninterrupted for as long as possible, this is where the type of content matters. We know that for example gaming or video streaming sites tend to keep people on their page much longer than others.”
Mr. Segura’s article, and many others, describe the rapidly developing abuses and dangers of crypto miners:Â
– According to ESET, a known vulnerability in Microsoft IIS 6.0 (CVE-2017-7296) is being exploited to install miner scripts on unpatched Windows servers.
- A tech support scam is delivering Coinhive’s Monero Miner via an EI TEST campaign, the details of which are described in this Trend Micro blog post.Â
– Using a known abuse tactic that exploits IE zombie script, the mining can actually continue even after users navigate away from the website containing the script.
– Last but not least, the user’s CPU is heavily taxed during the mining process as seen in a screen shot below captured while a script was running. The system usage becomes more noticeable when using a cell phone or a tablet with less processing resources.
 While the malicious-or-not classification of the cryptocurrency mining services is still being debated, the fact remains that the scripts currently seem to be making more appearances on less than reputable sites, or, in the case of Showtime, to be used in less than ethical ways on reputable sites. As usual, when there’s money to be made, there’s no shortage of creative and dubious uses developing alongside the legitimate ones. Malware Patrol has developed a new Anti-Mining Data Feed to provide our customers with the option of protecting or warning their customers against these resource-draining scripts, or conducting their own research. The feed features sites currently running the Coinhive and JSE Coin scripts – 15,500 entries and growing – and is available for free to our SMB and Enterprise customers. It is updated twice a day and is available in the following formats:Â
While the malicious-or-not classification of the cryptocurrency mining services is still being debated, the fact remains that the scripts currently seem to be making more appearances on less than reputable sites, or, in the case of Showtime, to be used in less than ethical ways on reputable sites. As usual, when there’s money to be made, there’s no shortage of creative and dubious uses developing alongside the legitimate ones. Malware Patrol has developed a new Anti-Mining Data Feed to provide our customers with the option of protecting or warning their customers against these resource-draining scripts, or conducting their own research. The feed features sites currently running the Coinhive and JSE Coin scripts – 15,500 entries and growing – and is available for free to our SMB and Enterprise customers. It is updated twice a day and is available in the following formats:Â
– BIND – CSV – plain text – Hosts file – MaraDNS – RPZ DNS XFR – Snort – Squid – SquidGuard
Our current customers interested in this data should contact us to inquire about setting the feed up in your portal. Not a Malware Patrol customer yet? Contact us to discuss your threat data needs and to arrange a free data evaluation period.
Andre Correa
Co-Founder, Malware Patrol
 Information Security and Threat Intelligence Professional whose qualifications include in-depth knowledge of Internet technologies, current cyber security landscape, incident response, security mechanisms and best practices. He founded the Malware Patrol project in 2005. The company is helping enterprises around the world to protect themselves from malware and ransomware attacks through some of the most comprehensive threat data feeds and block lists on the market.
Information Security and Threat Intelligence Professional whose qualifications include in-depth knowledge of Internet technologies, current cyber security landscape, incident response, security mechanisms and best practices. He founded the Malware Patrol project in 2005. The company is helping enterprises around the world to protect themselves from malware and ransomware attacks through some of the most comprehensive threat data feeds and block lists on the market.
