PHISHING THREAT INTELLIGENCE
Protect and Educate
Fight Against Phishing Attacks
The phishing attack is one of the most common cyber threats and for several years, phishing has been one of the main techniques used by cybercriminals to target both individuals and companies for profit or other motives. Additionally, phishing has become the primary vehicle for ransomware delivery. Phishing schemes often include spoofed email addresses, compelling or relevant content for the recipient, along with links to websites that appear to be legitimate. Social engineering tactics have evolved significantly making it difficult for even security professionals to recognize every phishing attempt that comes their way.
Phishing attacks remain one of the top cyber menaces, accounting for 90% of data breaches.
Malware Patrol offers threat intelligence to help our customers protect their users and networks from phishing attacks. We collect phishing URLs from several sources – crawlers, emails, spam traps, and more – to ensure coverage of the most current campaigns. Our quality assurance process involves a mix of automated mechanisms and human revision that result in both a lower false-positive rate and a higher detection of techniques that evade machine detection. In addition, confidence scores are included to help further classify and prioritize indicators. Finally, for ease of use, we can distribute the data in formats that allow for easy integration into a wide variety of security tools and platforms.
Even More Phishing Data
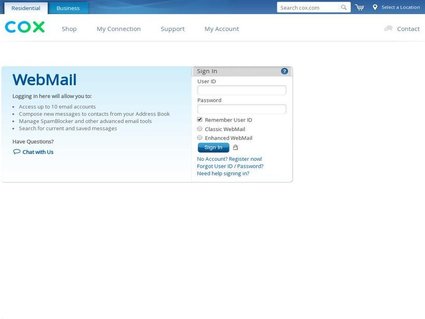
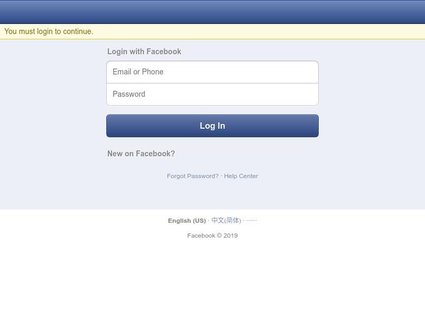
(1) We capture and store full JPEG images of the phishing websites in our feed. These screenshots are accompanied by perceptual hashing data. This image-based data can be used to teach your AI and/or machine learning tools as well as to educate employees about phishing.
(2) We record the raw HTML content of the phishing websites. This information can be used in the creation and improvement of rules for web gateways and email filtering systems, as well as the training of AI/ML detection systems and the augmentation of awareness training programs.
The screenshots and perceptual hashes and raw HTML data are offered as two separate add-ons to the phishing feed. Each of these are accessed via an AWS S3 bucket with AWS SNS as one of the available alert options.
Data Feed Details
CONTENTS
– Phishing URLs, with industry classification, for 300+ international brands
Optional add-ons:
– Image bank of phishing screenshots & perceptual hashes
– Raw HTML content of phishing websites
FORMATS
– JSON
– Other formats available upon request
FEATURES
– Free evaluation
– Hourly updates
– Full-use commercial license