FortiGate NGFWs deliver industry-leading enterprise security for any edge at any scale with full visibility and threat protection. Organizations can weave security deep into the hybrid IT architecture and build security-driven networks to achieve:
- Ultra-fast security, end to end
- Consistent real-time defense with FortiGuard Services
- Excellent user experience with security processing units
- Operational efficiency and automated workflows
Malware Patrol offers (5) feeds formatted for integration into the FortiGate Security Fabric (External Connectors/Threat Feeds). Customers can choose the feed(s) that meet their needs:
- DNS-over-HTTPS (DoH) Servers (domains)
- Malicious Domains
- Malicious Hashes
- Malicious IPs
- Malware/Ransomware URLs
We have written configuration instructions for both connecting and enabling protection with Malware Patrol feeds. Please note that some of the functionalities covered in this guide require a subscription, such as FortiGuard AntiVirus for using Malicious Hashes.
Also, following the instructions in the FortiGate Administration Guide, we have mostly modified default settings and policies whenever adding Malware Patrol’s feeds. For logging or other purposes you may wish to create new ones instead. Additional resources are included at the end of this guide, including a link to FortiGate’s manual.
‘
Adding external threat data feeds to FortiGate
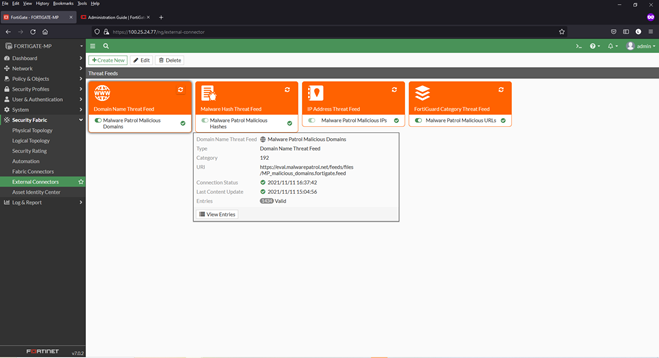
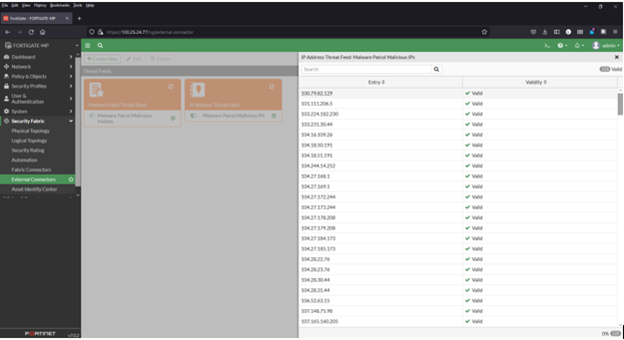
1) From inside the FortiGate interface, select Security Fabric > External Connectors. For this configuration guide, we have already added the Malware Patrol Malicious Hashes feed as an example, seen below.
2) Click Create New
3) Scroll down to Threat Feeds section
4) Select feed type to be added. Options are:
a. FortiGuard Category (for URL lists)
b. IP Address
c. Domain Name (for this example)
d. Malware Hash
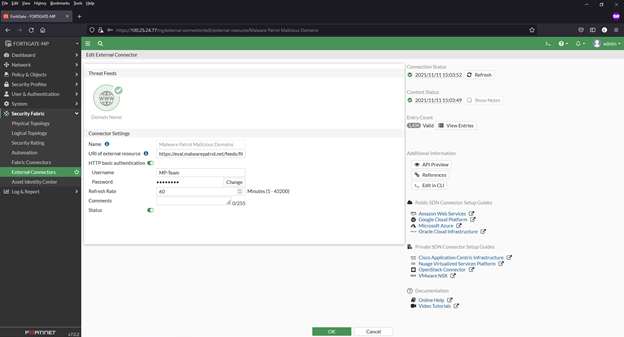
5) Complete the following in the fields on the next page:
- Feed name: We will use Malware Patrol Malicious Domains
- URL: You can find the URL of the Malware Patrol Malicious Domains data feed in the evaluation or customer portal
- Login credentials: Username and password for Malware Patrol evaluation or customer portal
- Refresh rate: We use 61 minutes as our feeds are updated hourly
6) Click OK to save. You will now see the new feed added to the list of connectors.
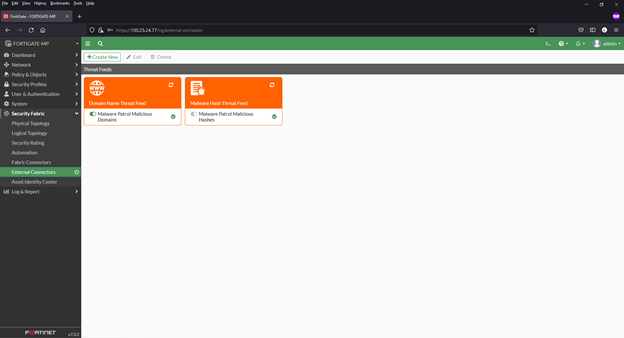
7) Click Create New to add any additional feed(s) you have. Instructions for each are the same as the previous example. For the examples in this how-to, we use the names below:
a. FortiGuard Category (for URL lists) – Malware Patrol Malicious URLs
b. IP Address – Malware Patrol Malicious IPs
c. Domain Name – Malware Patrol Malicious Domains
d. Malware Hash – Malware Patrol Malicious Hashes
8) Click the refresh button and hover over any feed to see details, including number of valid/invalid entries
9) Click View Entries to see the feed’s entries
Adding IP data feeds to firewall policies
1) Navigate to Policy & Objects > Firewall Policy
2) Click Create New
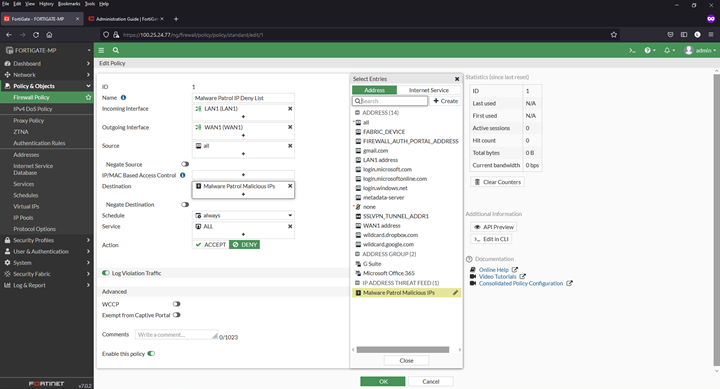
3) Complete the following in the fields on the next page:
- Name: We will use Malware Patrol IP Deny List
- Select incoming and outgoing interfaces: per your needs/environment
- Source: All
- Destination: Malware Patrol Malicious IPs list (menu appears on right, scroll down)
- Schedule: Always
- ServiceAll
- Action: Deny
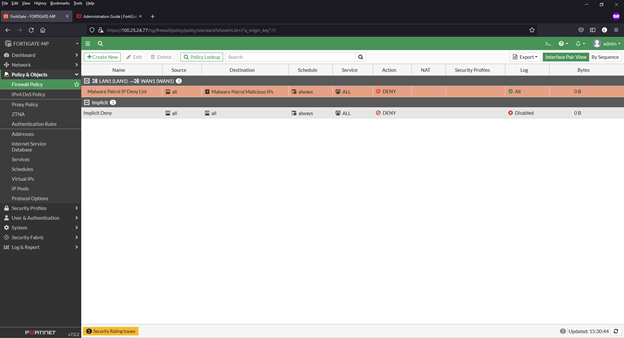
4) Click OK to save. New policy will appear in list
FortiGate policy details: https://docs.fortinet.com/document/fortigate/7.0.2/administration-guide/118003/policies
FortiGate video: https://youtu.be/dpvlQ0xU2NU
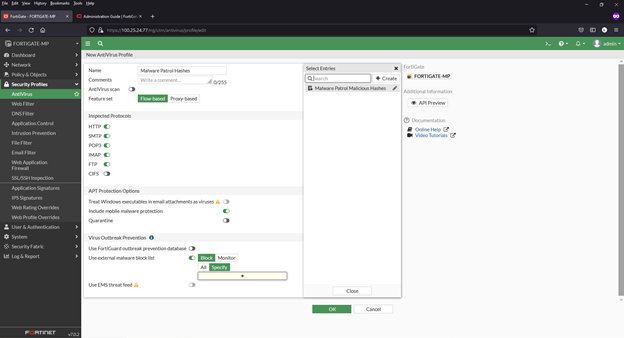
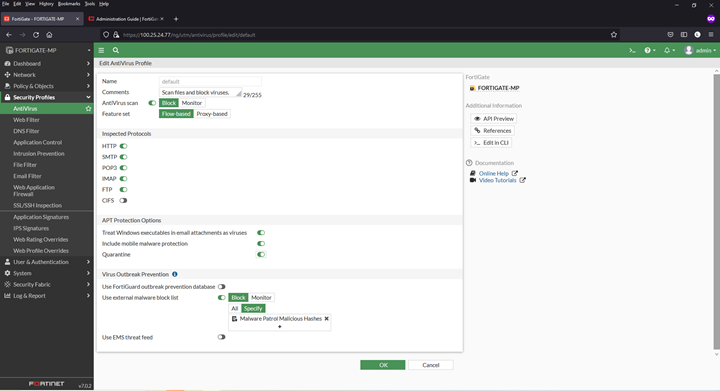
Adding an external malware blocklist (hashes) to the AntiVirus
1) Navigate to Security Profiles > AntiVirus
2) Click to edit the default profile
3) Enable Use external malware block list (toward bottom of page). Also enable Quarantine if desired.
4) Select ‘Specify’ in the Virus Outbreak Prevention
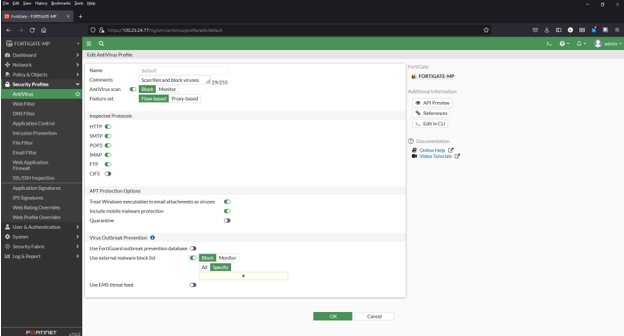
5) Click the + and select the Malware Patrol Malicious Hashes feed from the menu
6) Click OK to save
FortiGate AntiVirus details: https://docs.fortinet.com/document/fortigate/7.0.2/administration-guide/913906/external-blocklist-file-hashes
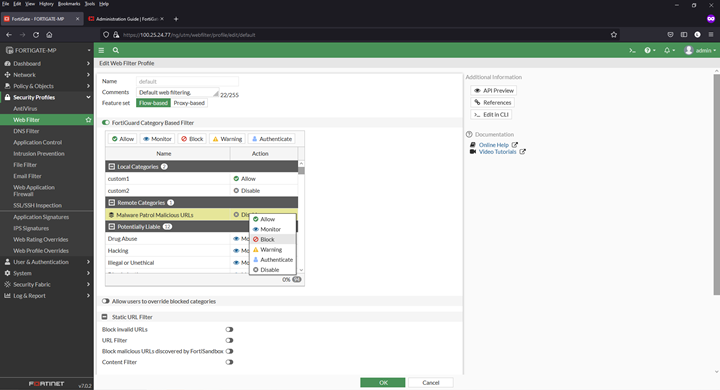
Adding a URL blocklist to the web filter
1) Navigate to Security Profiles > Web Filter
2) Click to edit the default profile
3) Select Malware Patrol Malicious URLs from FortiGuard Category Based Filter menu
4) Right click on Disable and select Block from dropdown menu
5) Click OK to save
FortiGate Web Filter details: https://docs.fortinet.com/document/fortigate/7.0.2/administration-guide/833698/web-filter
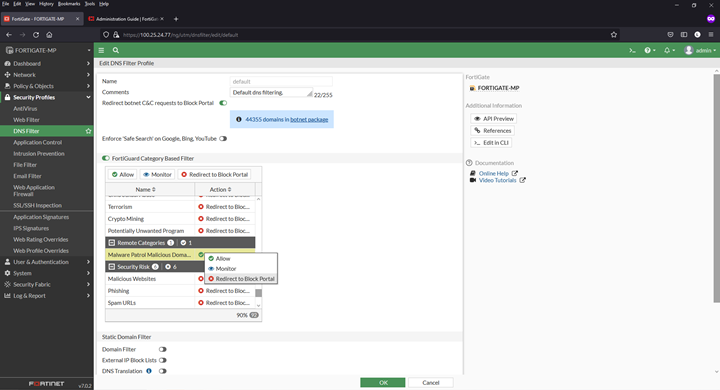
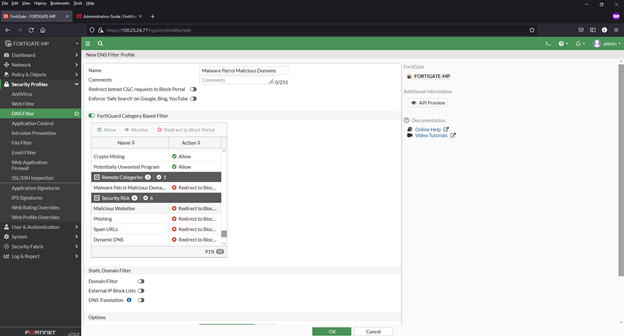
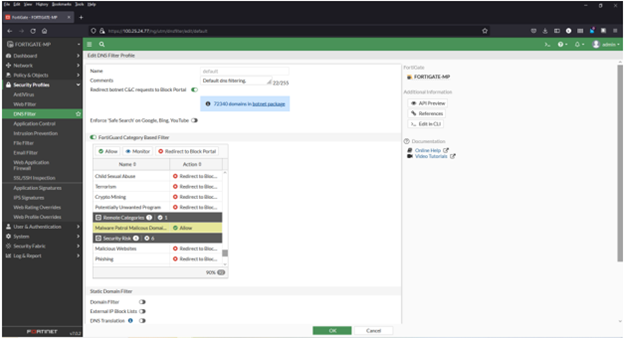
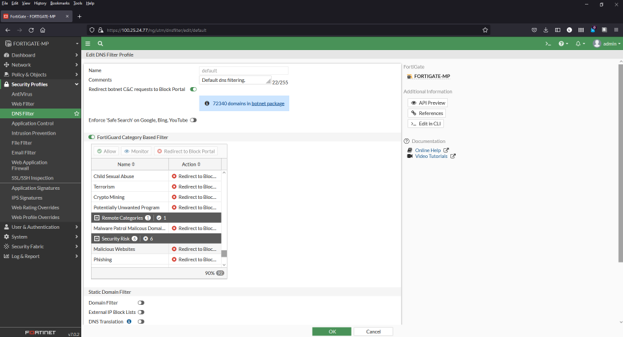
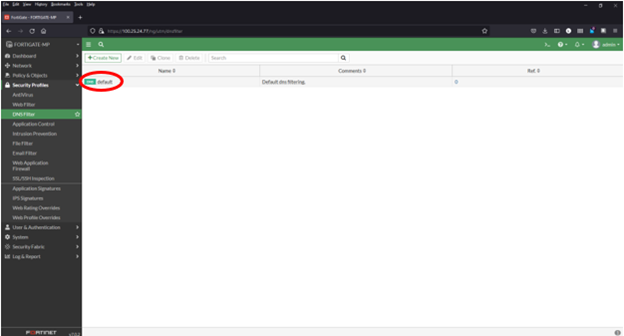
Adding a domain blocklist to the DNS filter
1) Navigate to Security Profiles > DNS Filter
2) Double click to edit the default profile
3) Select Malware Patrol Malicious Domains from FortiGuard Category Based Filter menu (scroll down to Remote Categories section)

4) Right click on Allow and select Redirect to Block Portal from dropdown menu
5) Click OK to save
FortiGate DNS Filter details: https://docs.fortinet.com/document/fortigate/7.0.2/administration-guide/605868/dns-filter
Additional resources
FortiGate Administration Guide: https://docs.fortinet.com/document/fortigate/7.0.2/administration-guide/954635/getting-started
FortiGate Administration Guide, threat data feeds: https://docs.fortinet.com/document/fortigate/7.0.2/administration-guide/9463
/threat-feeds
Excellent walk-through video for adding and enabling external threat feeds: Configure and use 3rd Party threat feeds on a FortiGate Firewall by GraniteDan https://youtu.be/CarI6_URN90
Share this post: